Validating User Flows to Protect Software Defined Network Environments
Por um escritor misterioso
Descrição
Software Defined Network is a promising network paradigm which has led to several security threats in SDN applications that involve user flows, switches, and controllers in the network. Threats as spoofing, tampering, information disclosure, Denial of Service, flow table overloading, and so on have been addressed by many researchers. In this paper, we present novel SDN design to solve three security threats: flow table overloading is solved by constructing a star topology-based architecture, unsupervised hashing method mitigates link spoofing attack, and fuzzy classifier combined with L1-ELM running on a neural network for isolating anomaly packets from normal packets. For effective flow migration Discrete-Time Finite-State Markov Chain model is applied. Extensive simulations using OMNeT++ demonstrate the performance of our proposed approach, which is better at preserving holding time than are other state-of-the-art works from the literature.

Chapter 6: Maintaining a Secure Environment, Weaving a Secure Web
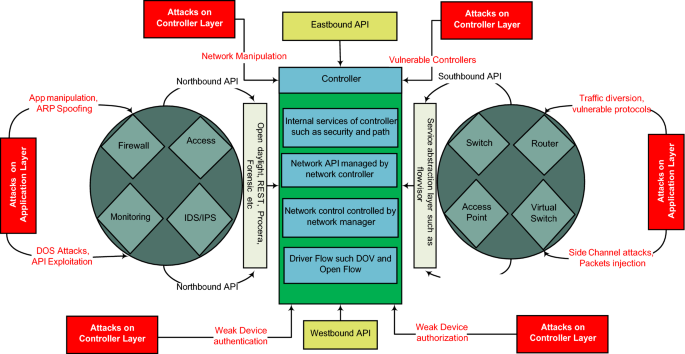
Security & Privacy in Software Defined Networks, Issues
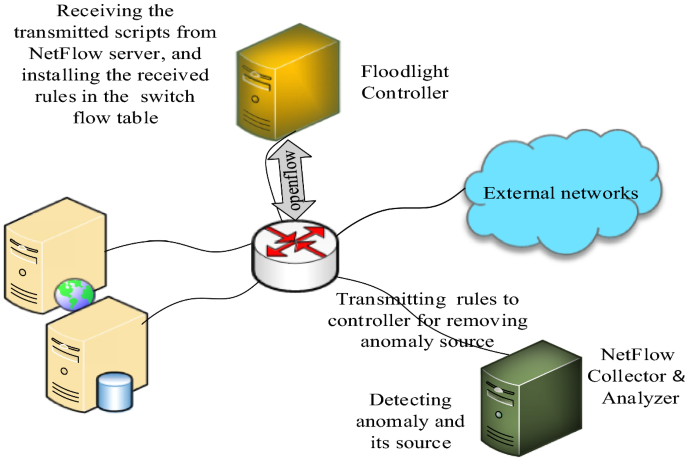
SADM-SDNC: security anomaly detection and mitigation in software
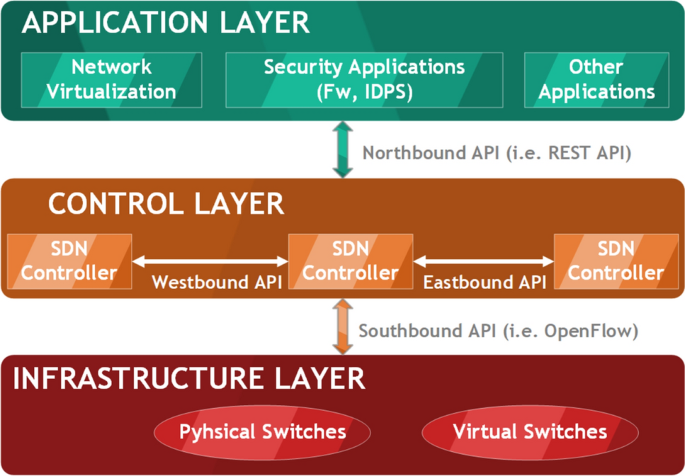
Flow-based intrusion detection on software-defined networks: a

Single Sign-On overview

Validating User Flows to Protect Software Defined Network Environments

Validating User Flows to Protect Software Defined Network Environments

Validating User Flows to Protect Software Defined Network Environments

Software defined wireless sensor networks application
How Netflix uses eBPF flow logs at scale for network insight

Electronics, Free Full-Text

Control Flow Diagram in Software Engineering: Symbols & Example
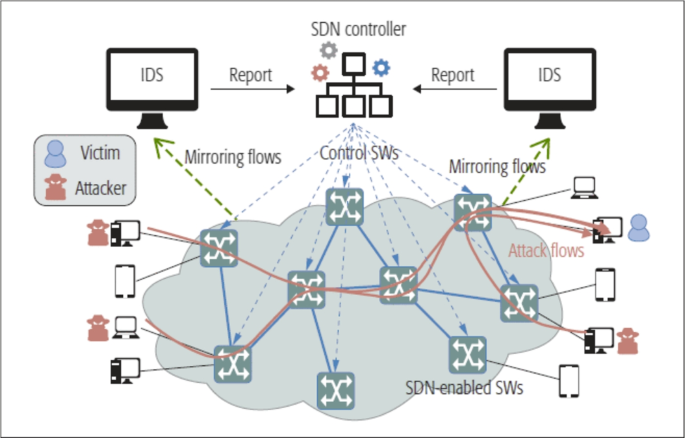
Software defined networks (SDNs) for environmental surveillance
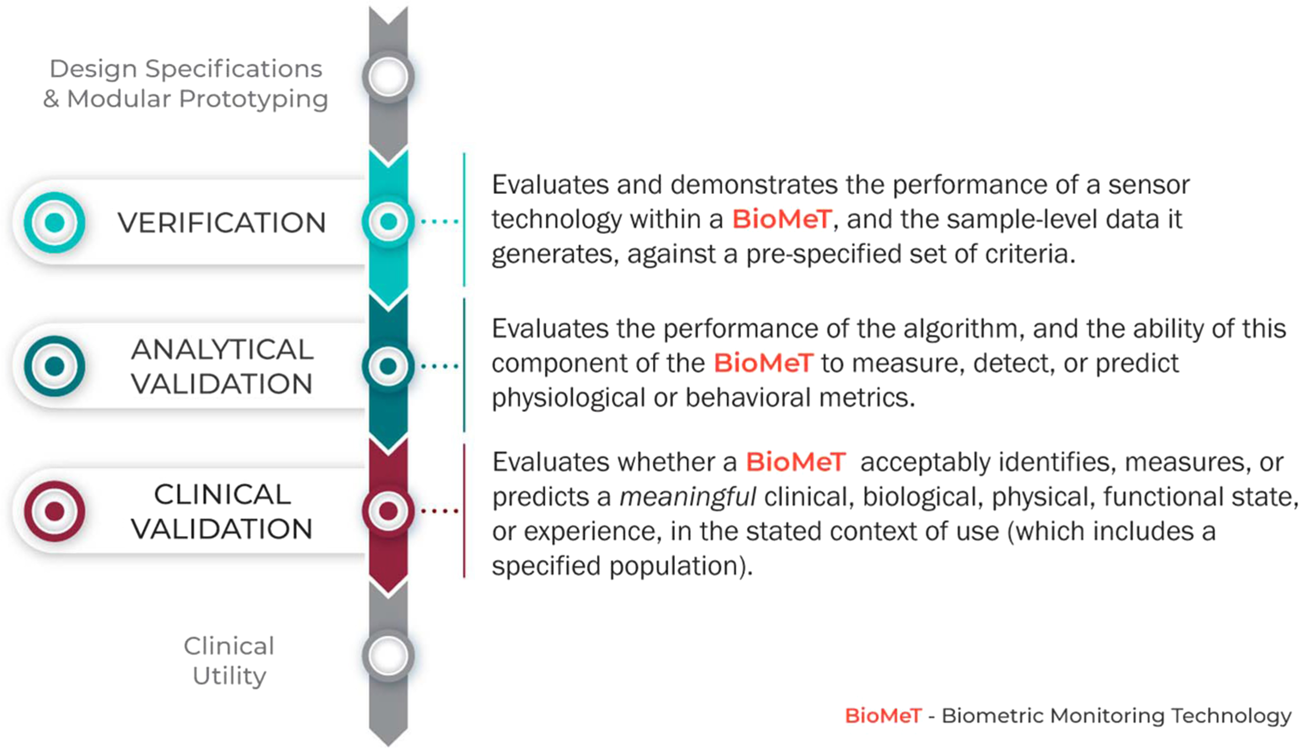
Verification, analytical validation, and clinical validation (V3
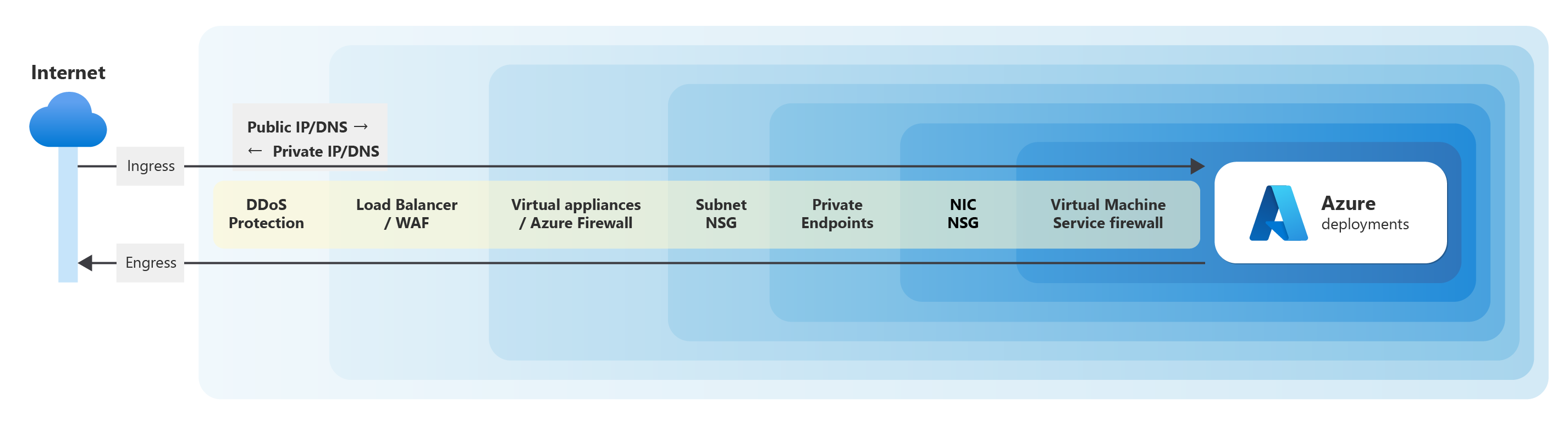
Recommendations for networking and connectivity - Microsoft Azure
de
por adulto (o preço varia de acordo com o tamanho do grupo)






