Malware analysis Suspicious activity
Por um escritor misterioso
Descrição

Using Python for Malware Analysis — A Beginners Guide

Malware Analysis Benefits Incident Response
A Basic Malware Analysis Walkthrough, by Dan Crossley
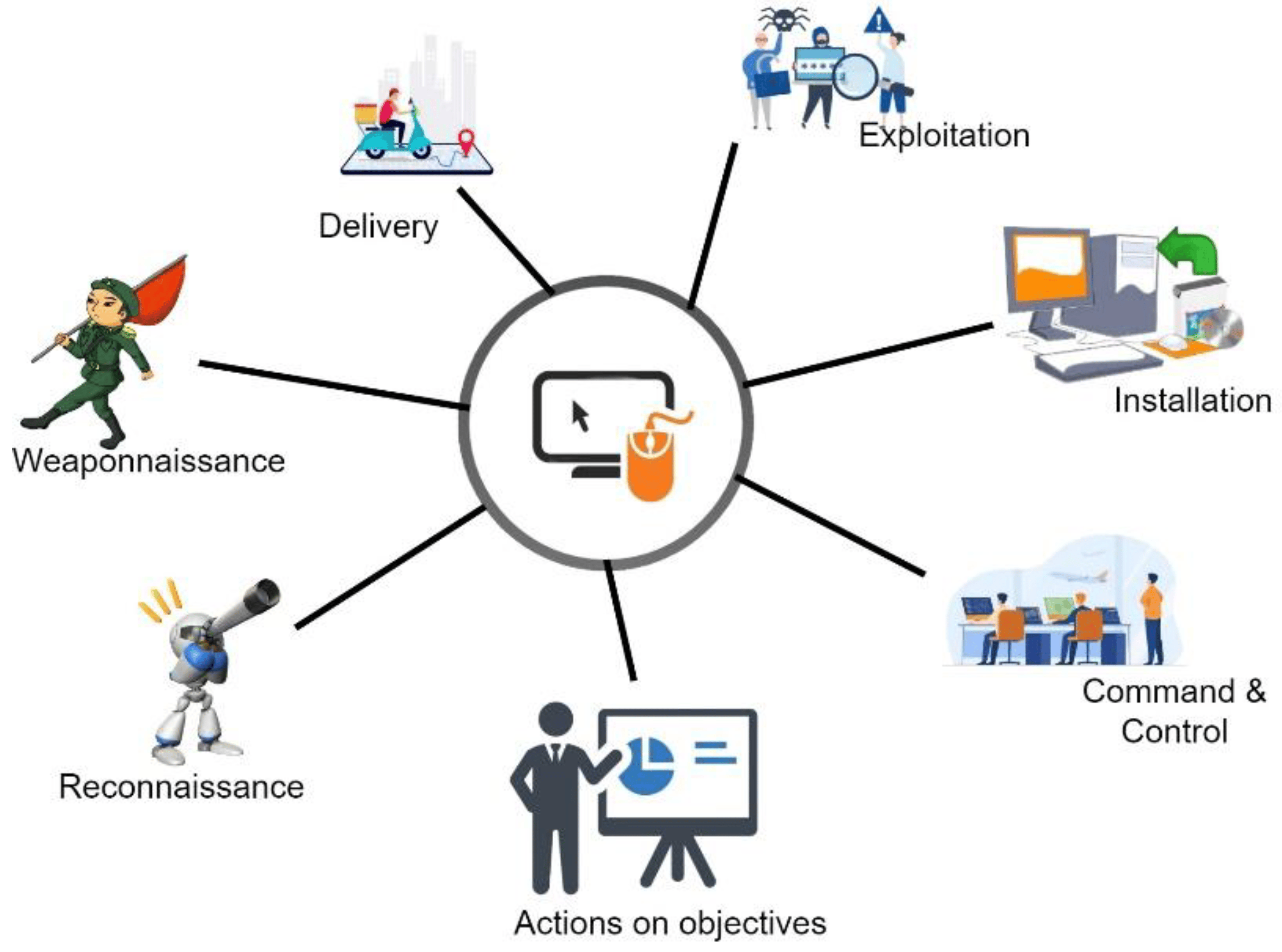
Symmetry, Free Full-Text
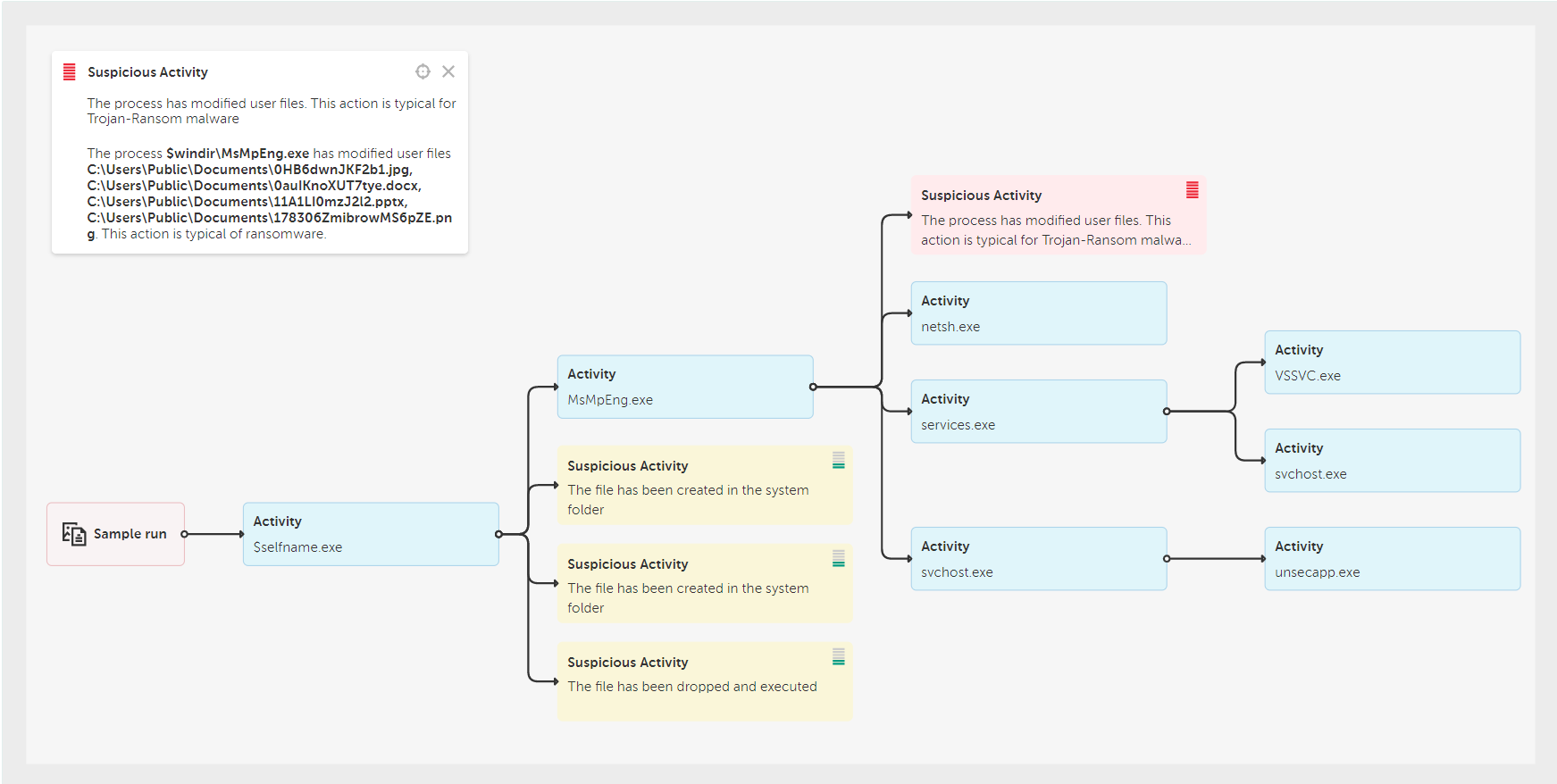
REvil ransomware attack against MSPs and its clients around the
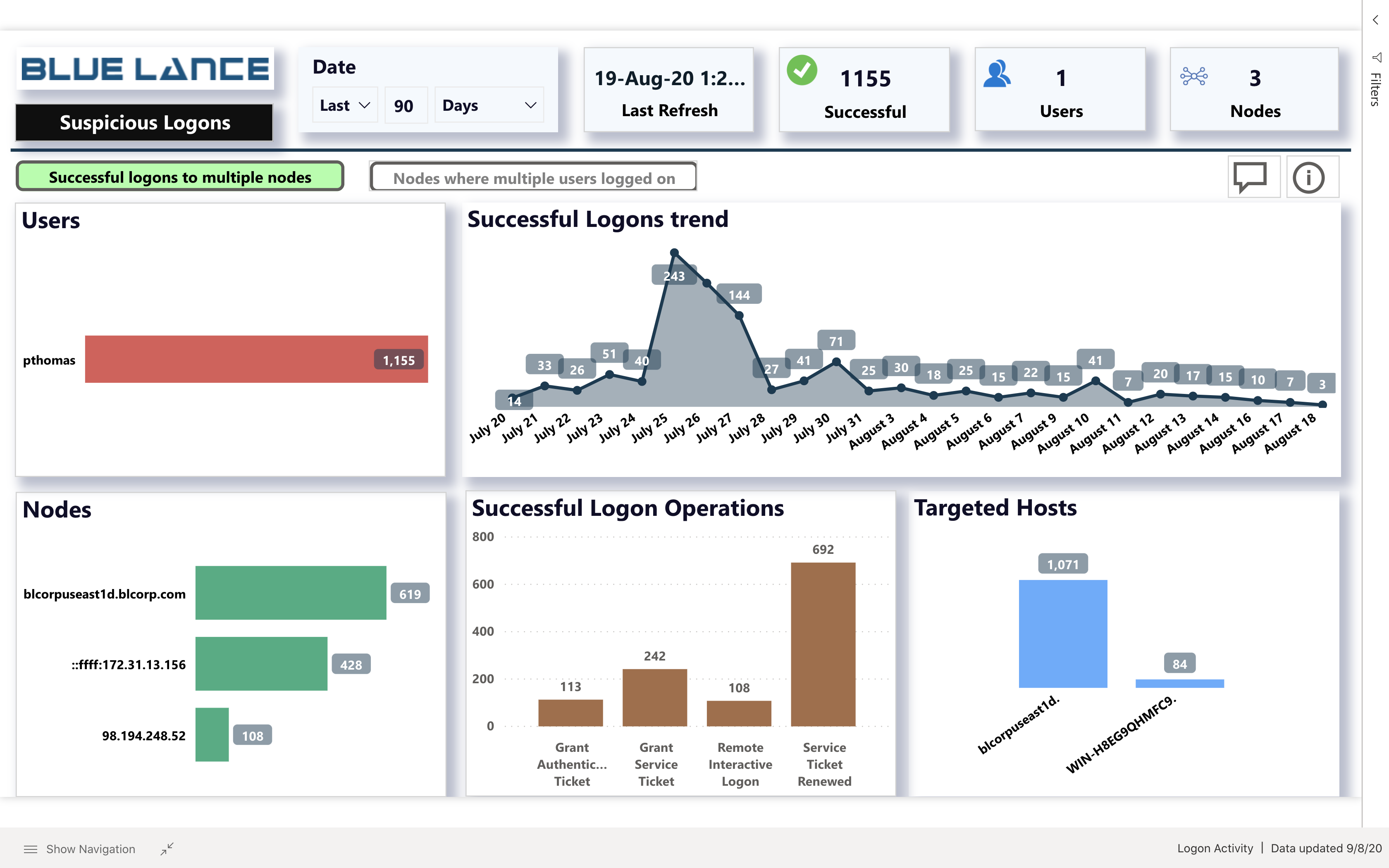
Suspicious Successful Logon Analysis

The Top 20 Malware Analysis Tools for 2024
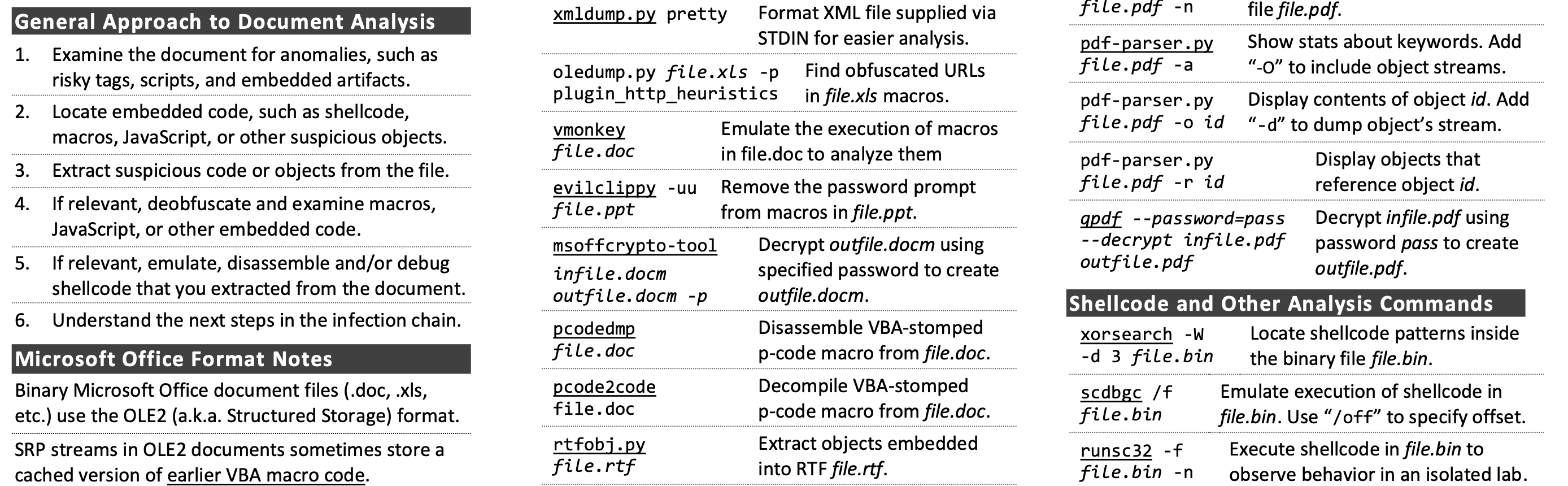
Analyzing Malicious Documents Cheat Sheet

Malware Analysis: Steps & Examples - CrowdStrike

Behavior-based malware analysis process as conducted by our

Malware Analysis: Steps & Examples - CrowdStrike
de
por adulto (o preço varia de acordo com o tamanho do grupo)