Malware analysis Suspicious activity
Por um escritor misterioso
Descrição
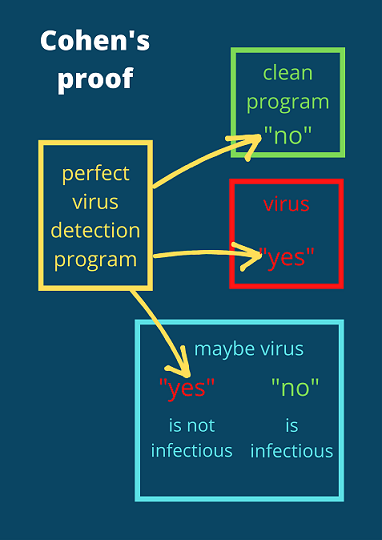
The real reason why malware detection is hard
Highlight, take notes, and search in the book

Mastering Malware Analysis: A malware analyst's practical guide to combating malicious software, APT, cybercrime, and IoT attacks, 2nd Edition
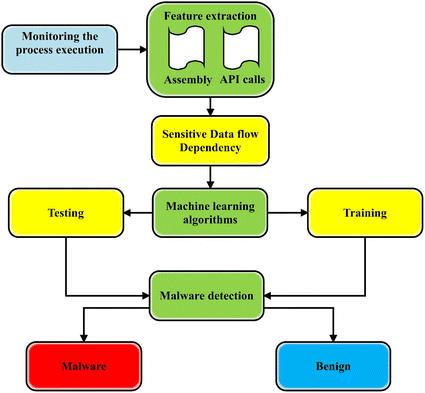
A state-of-the-art survey of malware detection approaches using
ChatGPT-Powered Malware Analysis 2023
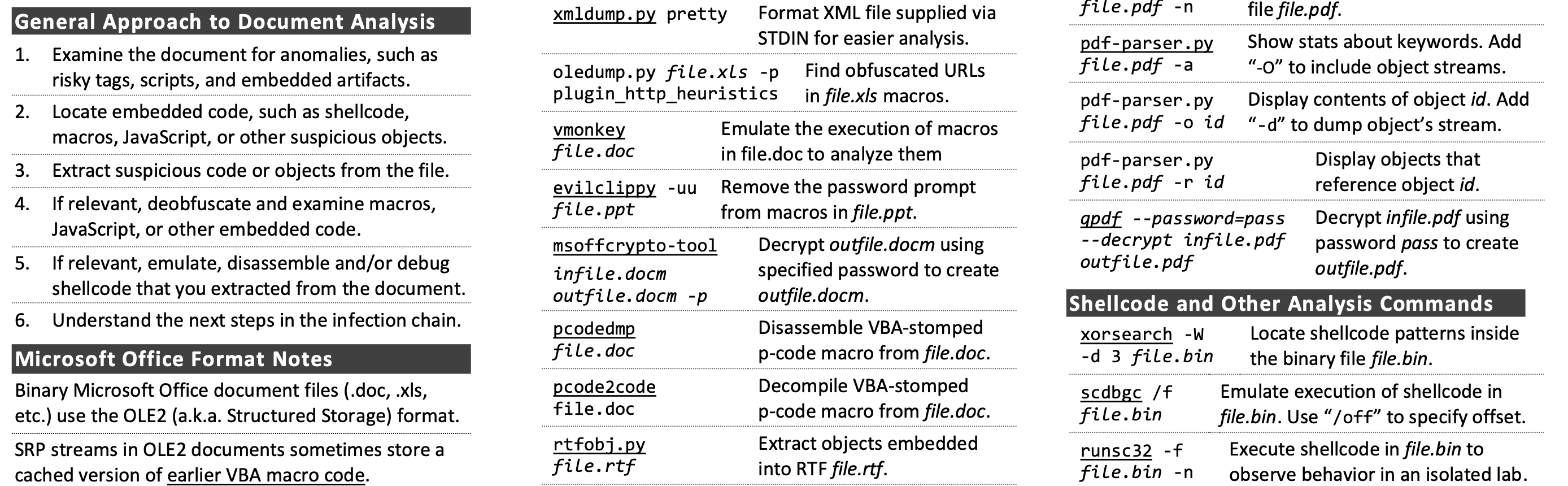
Analyzing Malicious Documents Cheat Sheet

Behavioral blocking and containment: Transforming optics into
Symmetry, Free Full-Text
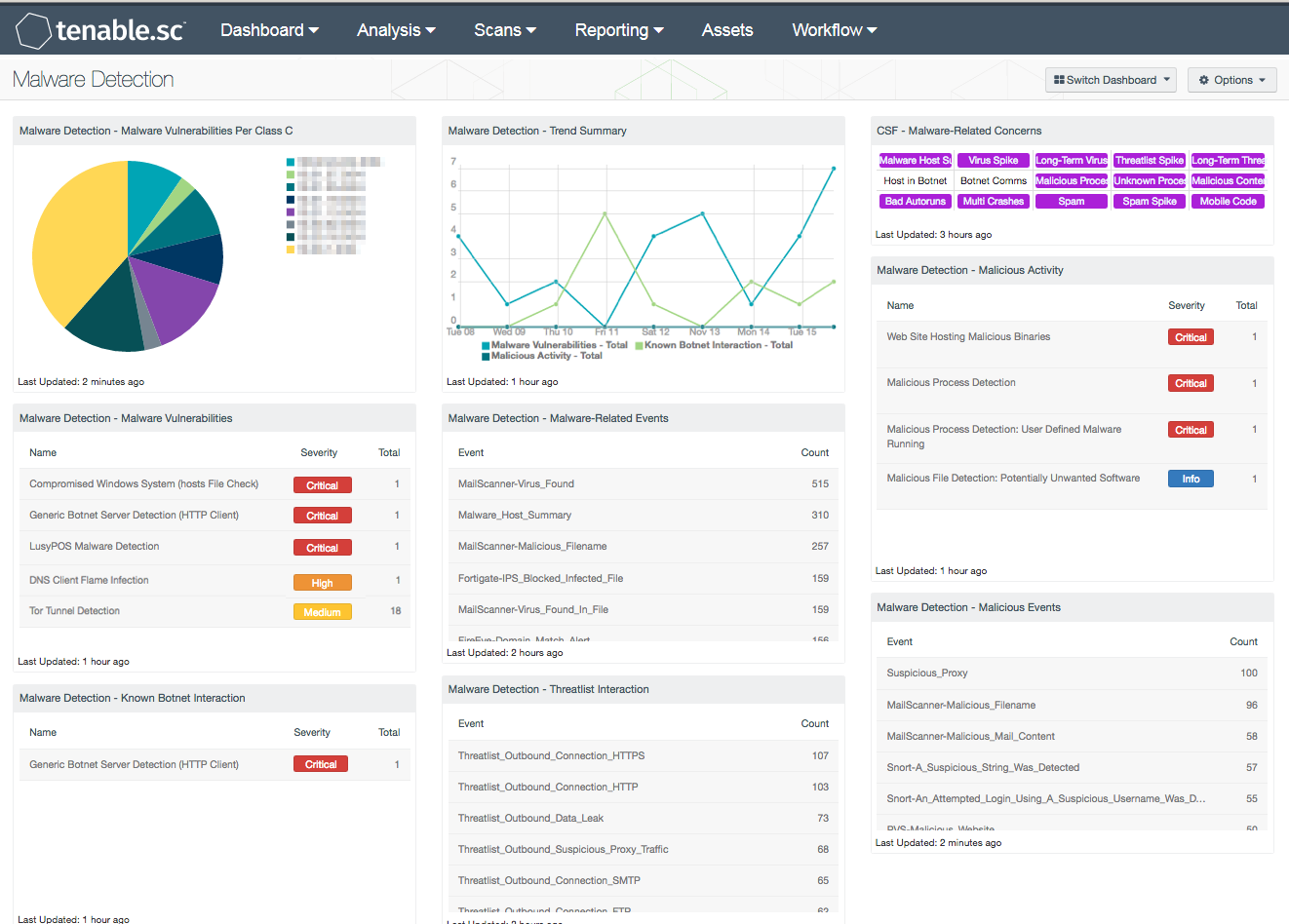
Malware Detection - SC Dashboard
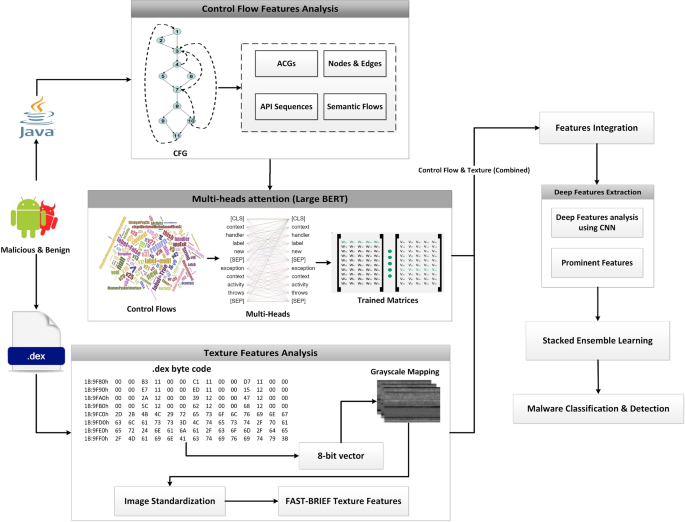
A malware detection system using a hybrid approach of multi-heads

How to Detect New Threats via Suspicious Activities

Intro to Malware Analysis: What It Is & How It Works - InfoSec
de
por adulto (o preço varia de acordo com o tamanho do grupo)