The SpiKey attack: How to copy keys using sound
Por um escritor misterioso
Descrição
The SpiKey attack: How one can copy a key using a phone recording of the sound of the clicks the key makes during insertion into a lock.

Experimental data on neurons with spike frequency adaptation (SFA) and

SpiKey: Beware of the Sound of Your Key

Two Years into the COVID-19 Pandemic: Lessons Learned
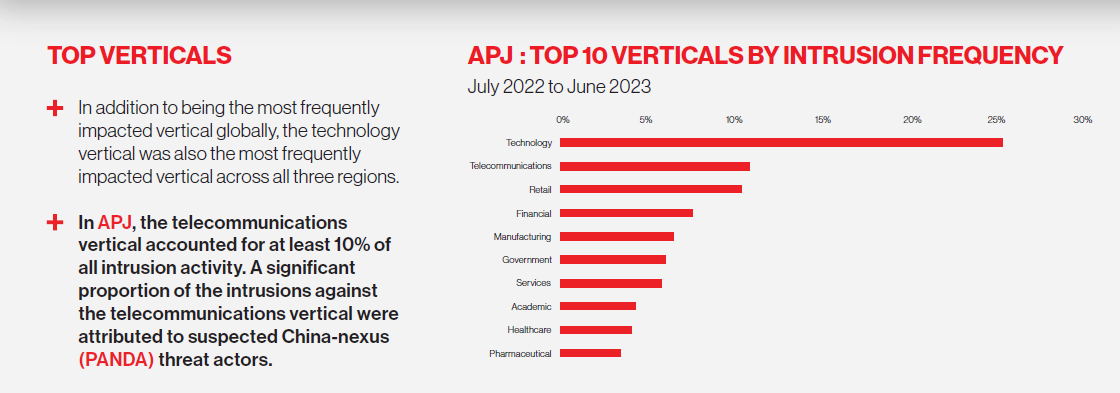
Identity-Based Attacks and Hands-on-Keyboard Activity on the Rise

The Best Songs of 2022

Spikey Attack Creates Duplicate Keys By Listening To Click Sounds

Basic Volleyball Rules and Terms - The Art of Coaching Volleyball

What is Malware? Malware Definition, Types and Protection

Basic Volleyball Rules and Terms - The Art of Coaching Volleyball

Hackers can now clone your keys just by listening to them with a smartphone
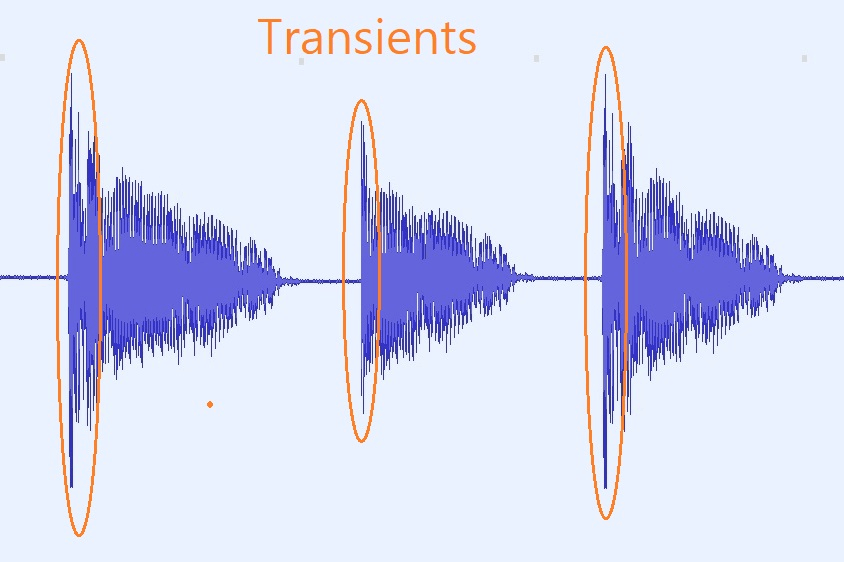
What are transients? How to deal with it in the mixing proces?

The Immortality Key

The SpiKey attack: How to copy keys using sound

Stealing Keystrokes With Sound - ThreatWire
de
por adulto (o preço varia de acordo com o tamanho do grupo)






