Suspicious User Controls
Por um escritor misterioso
Descrição

Enforcive Enterprise Security Suite - Compliance Solution from Precisely

Suspicious User Controls

Detect Potentially Suspicious Activity In Teams With Cloud App Security – Sam's Corner
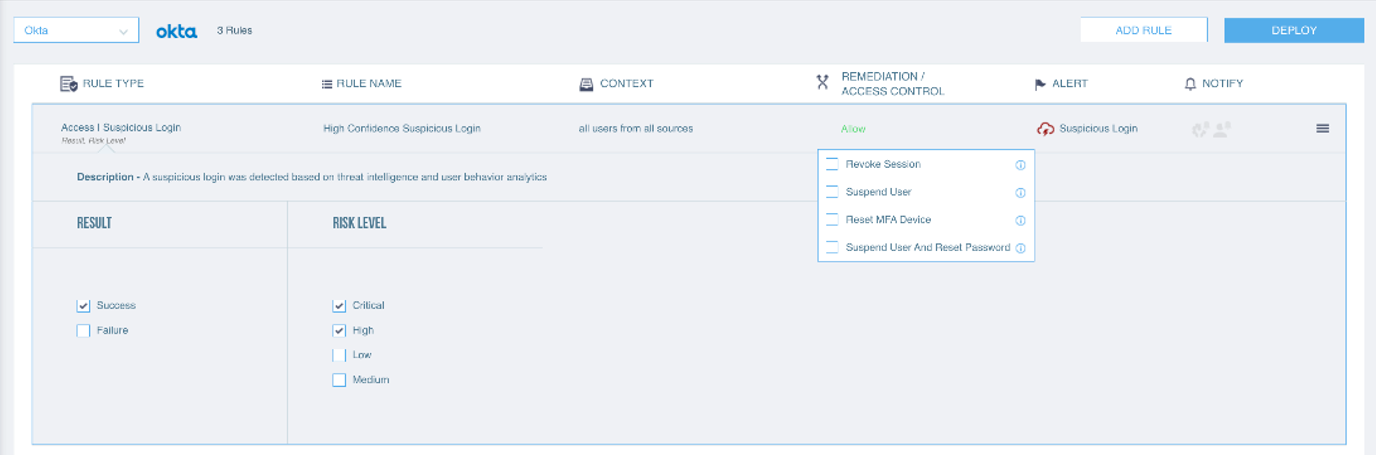
Suspicious Login Detection with your Cloud Identity Provider Through Proofpoint CASB

What Is Email Security? Definition, Benefits, Examples & Best Practices - Spiceworks
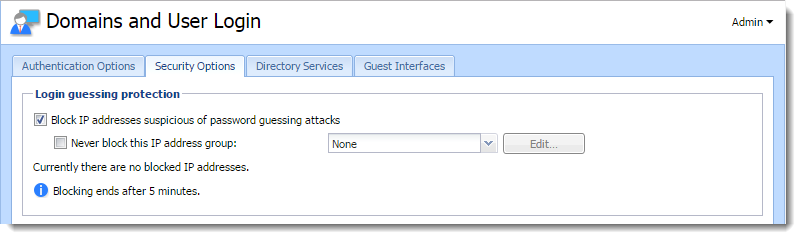
Protecting users against password guessing attacks
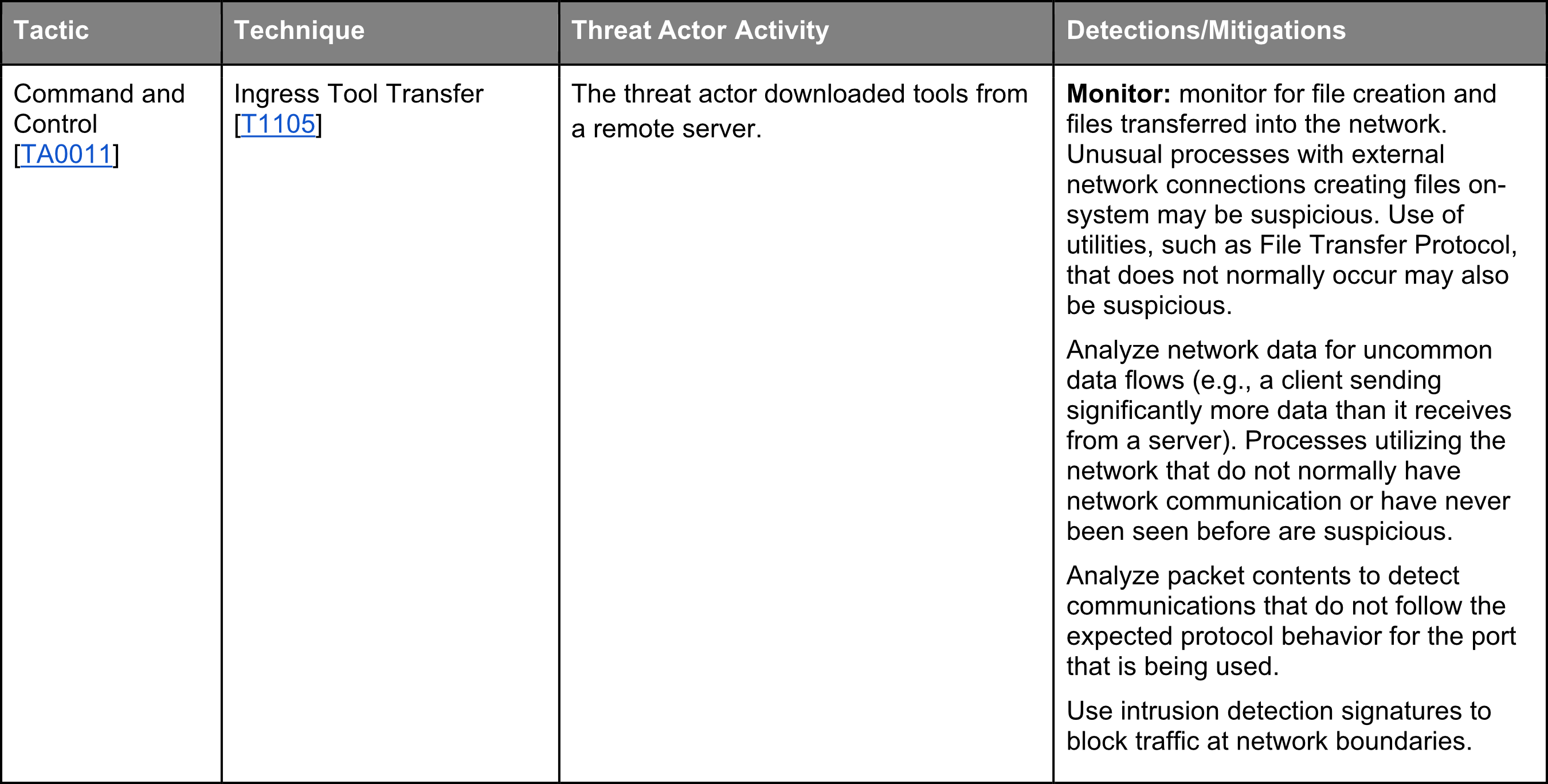
TRITON's Tactics and Techniques in the Enterprise domain + mitigations - Part 8 - SEQRED

DETEGO de-anonymizes fraud. Fraud detection only identifies suspicious

Set Up End User Alert Notifications

GSPBC-1036: Defense Evasion - Indirect Command Execution - GuardSight, Cybersecurity as a Service
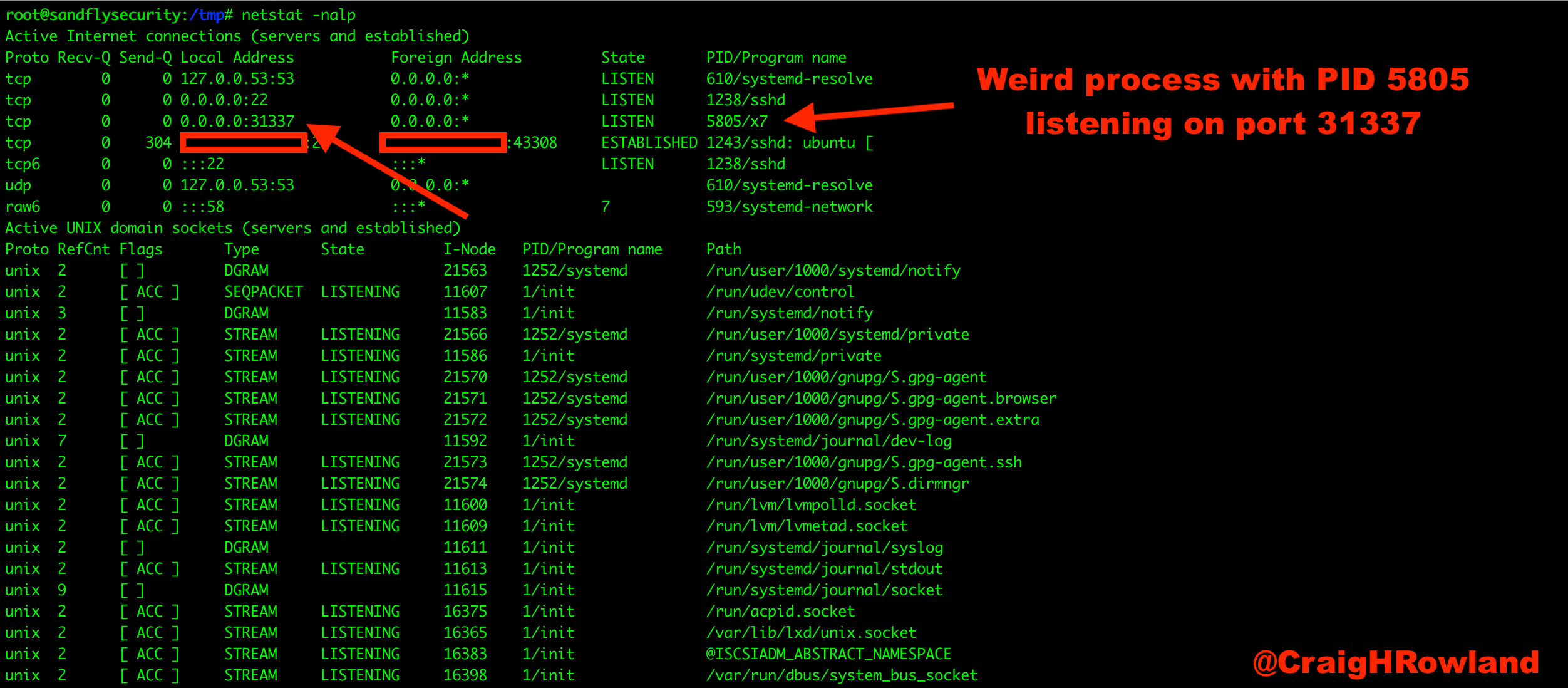
How to: Basic Linux malware process forensics for incident responders

PCI DSS Compliance Solution Brief
de
por adulto (o preço varia de acordo com o tamanho do grupo)






