The Newest Variant of the Astaroth Trojan Evades Detection in the
Por um escritor misterioso
Descrição
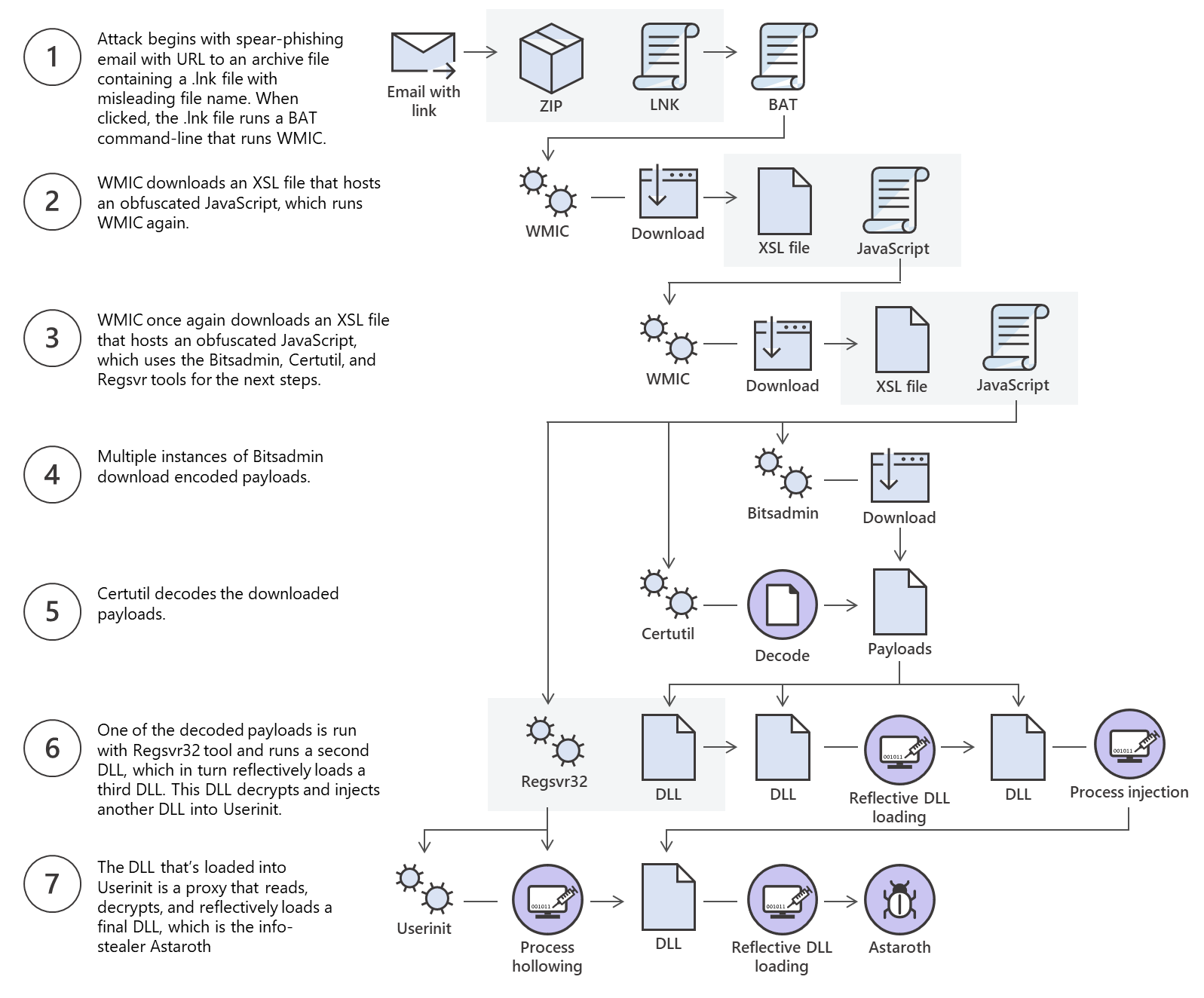
In this malware research, we explain one of the most recent and unique campaigns involving the Astaroth trojan. This Trojan and information stealer affected Europe and especially Brazil through the abuse of native OS processes and the exploitation of security-related products.

Research, Malicious Life Network

Out of sight but not invisible: Defeating fileless malware with behavior monitoring, AMSI, and next-gen AV

Research, Malicious Life Network

New Astaroth Trojan Variant Exploits Anti-Malware Software to Steal Info
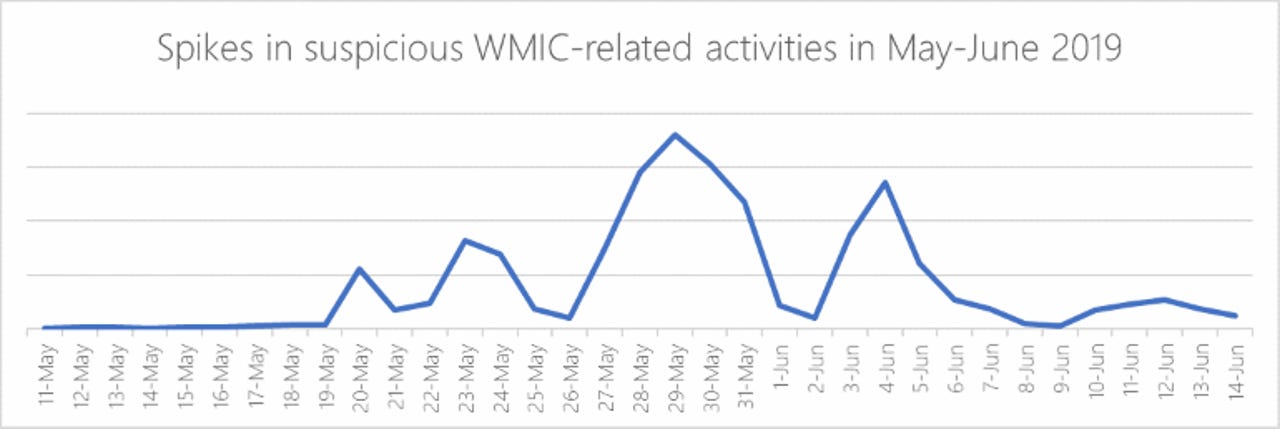
Microsoft warns about Astaroth malware campaign

Cybereason Nocturnus, Authors, Malicious Life Network

IFinder Info Solutions

NGAV Redefined: 9 Layers of Unparalleled Attack Protection

Malware Attacks: Definition and Best Practices
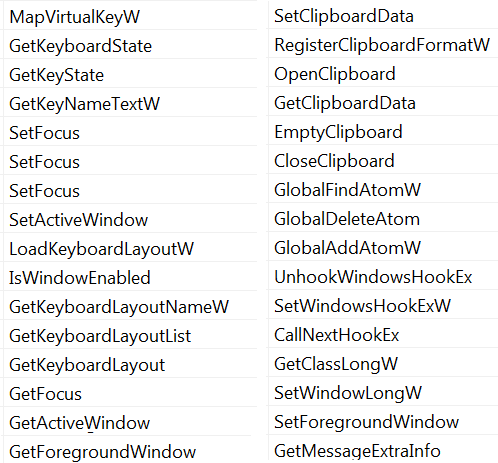
Astaroth Malware Uses Legitimate OS and Antivirus Processes to Steal Passwords and Personal Data

Trojan - Security Intelligence
Microsoft Discovers Fileless Astaroth Trojan Campaign
Astaroth Malware Uses Legitimate OS and Antivirus Processes to Steal Passwords and Personal Data

Command-and-Control (C&C) - Security Intelligence
de
por adulto (o preço varia de acordo com o tamanho do grupo)